|
Vulnerability Test Configuration |
|
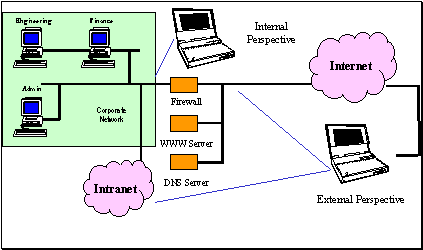
During the testing process, Cutting Edge Solutions professionals scan the financial institution's network from the perspective of a knowledgeable attacker using Cisco’s Net Sonar vulnerability scanning and network mapping system (illustrated above). The external scan focuses on security issues from the perspective of an attacker located outside of the network. The process consists of the phases described below: · Mapping - Networks are constantly changing to meet financial institution's requirements imposed on them by the need for increased productivity, access to information, and communications. These dynamic and ongoing changes inadvertently increase the security risk of an organization. The mapping phase is divided into the following two actions; · Host Discovery - an electronic inventory of the systems on your network. · Service Discovery - an electronic inventory of the services on each system. · Vulnerability Analysis - Vulnerability Measurement and Data Collection is the exploitation of network vulnerabilities to systematically measure the vulnerability state of the overall electronic perimeter. We measure and record vulnerability data for each system tested without causing disruption or interference to the systems being probed. · Reporting identifies network-computing equipment and security vulnerabilities associated with each device and security holes before they are used against the financial institution. · Target Analysis determines the financial institution's visibility from the outside; correlates network maps and identifies potential vulnerabilities. This phase provides insight into both the potential of a successful attack and the likelihood that system administrators would detect such an attack. · Data Analysis and Reporting provides the financial institution an assessment of the existing security architecture and actions to be taken to improve any deficiencies. Our reports are intended to be useful to network engineers, system administrators and executive management. |
When you are ready to have an affordable Intrusion - Vulnerability test of the Internet connection to your network system, please complete the Intrusion - Vulnerability Test Proposal Request Form. The test will take about two weeks from the time we received your authorization to the executive management letter. |