|
Security as an Operational Process |
|
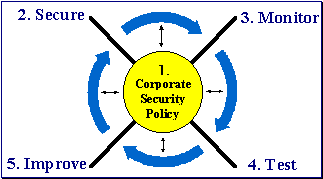
The basis for any security model is the financial institution's security policy. This forms the hub upon which to center the Security Wheel. The Security Wheel is a four-step process: 1. Secure the system. Historically, this has been done through "point" solutions such as identification/authentication measures, encryption software, and firewall technologies. The configuration metrics from these products serve to identify the granularity with which the corporate security policy is implemented. 2. Monitor the network to determine the active threat to corporate assets. Attacks on the network can occur within the secured perimeter from a disgruntled employee or from the outside such as from a hacker. Monitoring the network traffic will provide both internal and external attack metrics which, in turn, can validate if the "right" corporate security policy has been implemented. 3 Test the effectiveness of the security safeguards in place. This testing will provide vulnerability metrics with respect to the current security posture of the network and the security response procedures in place. 4. Improve the corporate security by taking all of the metrics that have been collected and perform an analysis. This analysis takes into effect the results of monitoring and testing, the criticality of the systems affected, and the current security policy.
When you are ready to have an affordable Intrusion - Vulnerability test of the Internet connection to your network system, please complete the Intrusion - Vulnerability Test Proposal Request Form. The test will take about two weeks from the time we received your authorization to the executive management letter. |